Vulnerabilities—exploitable weaknesses in application code—are used to facilitate attacks that can lead to data theft, malware injection and server takeover, among other consequences.
Vulnerability management is the process of rooting out and eliminating these weaknesses before they’re abused. It’s typically achieved through the following methods:
Vulnerability scanning involves using either a software or hardware-based scanner to locate soft spots in your code that can be exploited by known attack vectors. Soft spots are typically a result of unsanitized code that permits illegal inputs.
Scans involve periodic pen tests and code reviews to uncover weak spots in your application, followed by code updates to remove vulnerabilities. Code is rescanned afterward to ensure that vulnerabilities have been weeded out. This code review and modification cycle should be conducted after code updates and anytime new attack vectors that could endanger your application are discovered.
As a whole, vulnerability scanning comes with several operational issues. For one, new vulnerabilities continually pop up, making scanning a frequent and resource-intensive process. Moreover, complete code sanitization is rarely achieved, as the body code usually exists in a continual state of change. This is on top of the fact that it’s impossible to predict all attack scenarios.
Lastly, vulnerability scanning cannot help with rapid responses to newly uncovered (zero-day) threats. This is crucial, as most exploits take place soon after new vulnerabilities are made public. Response time to such threats becomes a key component of any vulnerability management strategy—one that can’t be addressed by a prolonged cycle of code review and sanitization.
Patching newly discovered vulnerabilities relies on a third-party (usually a software’s creator) to develop and test patches for their software. Your security and DevOps teams are responsible for deploying the patches.
Similar to vulnerability scanning, patch management’s Achilles heel is its lack of responsiveness.
Typically, patching delays occur as a result of:
Consequently, fully patching a vulnerability can take days, weeks, or sometimes even longer—especially if there is a concern that a patch might affect your application’s core functionalities.
As a rule of thumb, the longer the patch process takes, the more likely it is that the vulnerability has already been exploited. Often by the time a patch is deployed it’s already too late. While patching is always considered best practice, this is why it should never be the only/main component of any vulnerability management strategy.
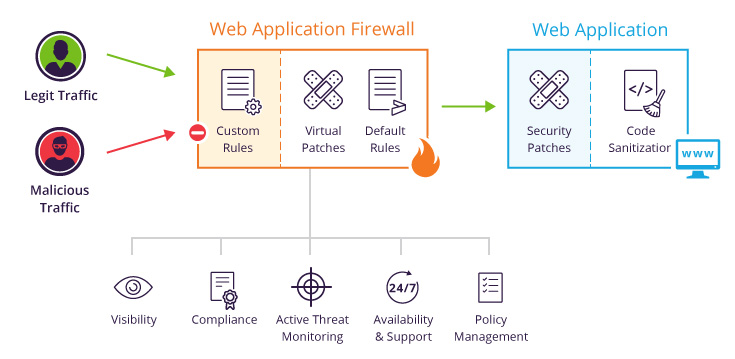
See how Imperva Web Application Firewall can help you with vulnerability management.

Input validation/sanitization is the process of deploying a web application firewall (WAF) on the edge of your network. Here it’s able to review all incoming traffic to your application, filtering out malicious inputs that target security vulnerabilities.
Input validation effectively solves vulnerability scanning and patch management issues for the following reasons: